Secrets Scanners
The Archodex Agent can report on hardcoded secrets found by GitHub Secret Scanning. When enabled, secret values found in code repositories will be cryptographically hashed using the same account-specific salt value as secret values observed in runtime workload network activity. Archodex can then help you understand when the same secret values are both hardcoded and stored in secret management systems.
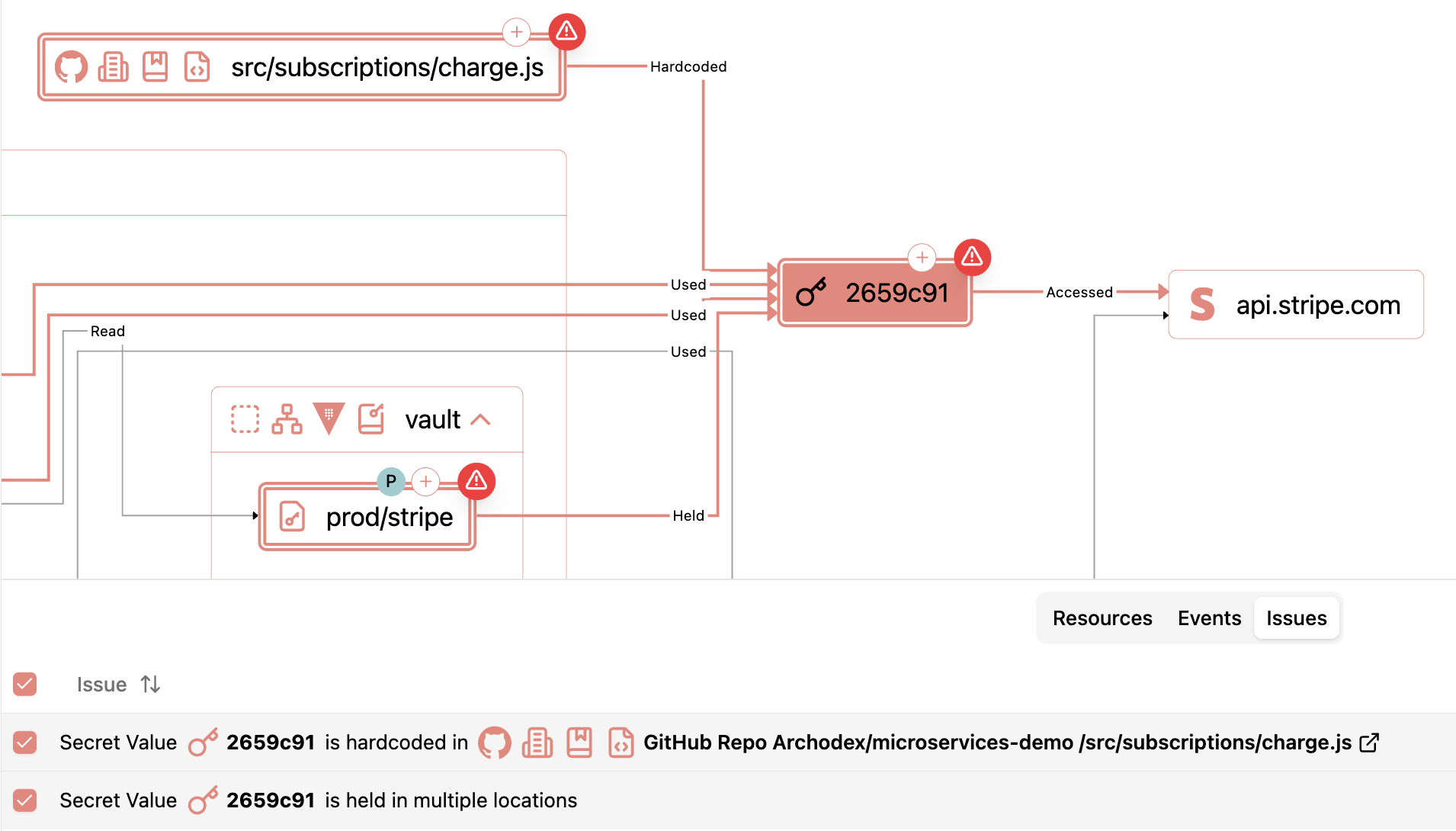
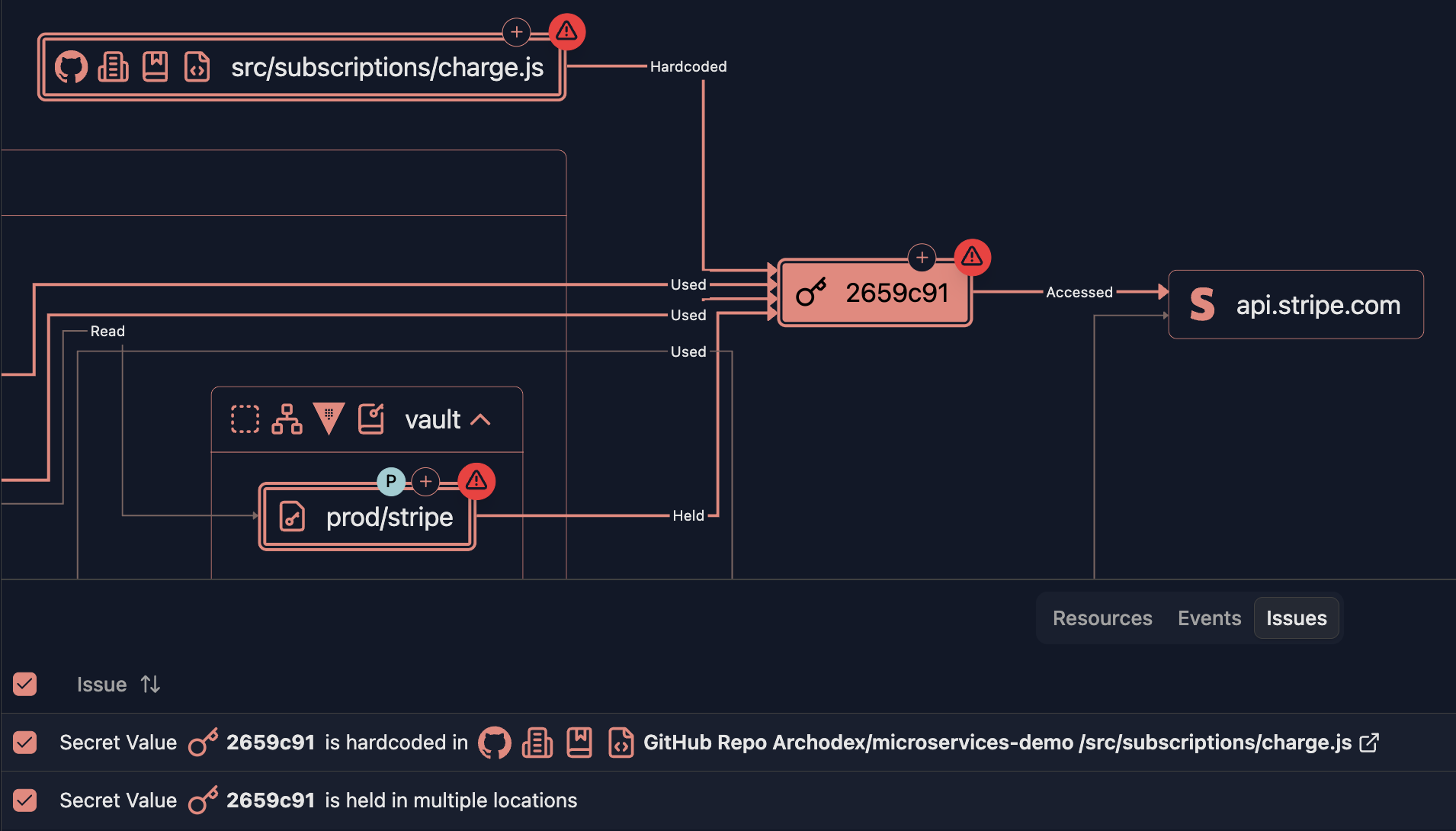
Example of a Stripe API key both hardcoded in a GitHub repository and stored in HashiCorp Vault
GitHub Secret Scanning
Section titled “GitHub Secret Scanning”Reporting hardcoded secrets requires two steps:
- Create a GitHub Token with the required permissions
- Run the Archodex Agent to pull scan results and report them to the Archodex Service
Create GitHub Token
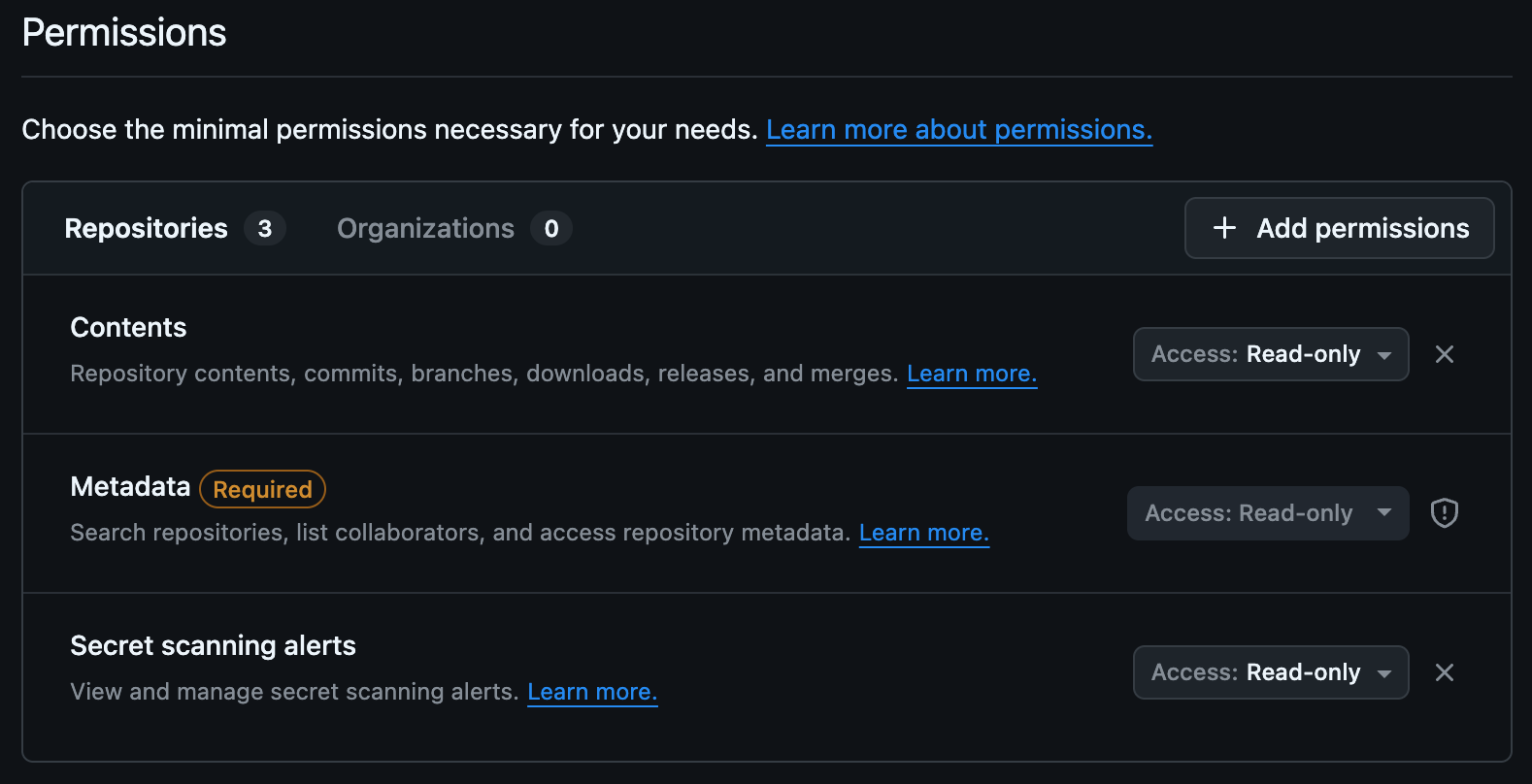
Section titled “Create GitHub Token”First, create a Fine-Grained GitHub Personal Access Token (PAT) for the Archodex Agent to use when querying the GitHub Secret Scanning API. The token must have at least read-only access to the “Contents”, “Metadata”, and “Secret scanning alerts” scopes for the repositories you want to pull scanning results from.
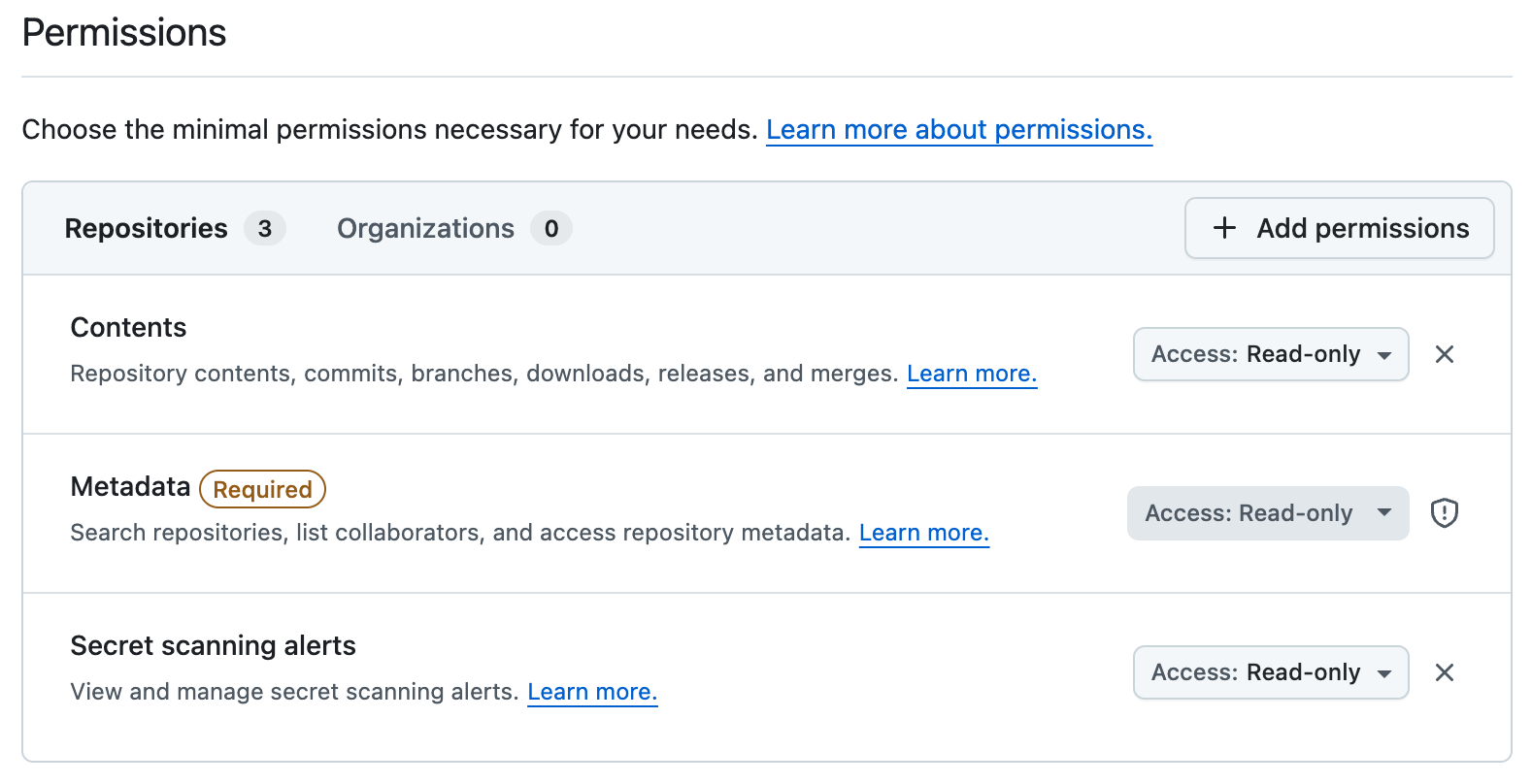
GitHub Secret Scanning API permissions required for the Archodex Agent
Run Archodex Agent
Section titled “Run Archodex Agent”Next, run the Archodex Agent:
$ docker run --rm -it \ ghcr.io/archodex/archodex-agent:latest secrets github \ --github-org <your_github_org> --github-token <your_github_token> \ --report-api-key <your_archodex_report_api_key>If you omit the --report-api-key argument, the Archodex Agent will run in log-only mode and will not report observations to the Archodex service. This is similar to the dry-run mode of many tools.
Reporting Frequency
Section titled “Reporting Frequency”We recommend running the Archodex Agent’s secrets command daily to record the latest results from GitHub Secret Scanning. This can easily be accomplished using your scheduling system of choice (e.g. cron jobs, GitHub Actions, cloud provider task schedulers).
When running via workflows you may find it easier to pass argument values using environment variables. The following environment variables can be used to provide the same values as the above command-line arguments:
ARCHODEX_REPORT_API_KEY: Your Archodex Report API KeyARCHODEX_SECRETS_GITHUB_ORGANIZATION: The GitHub Organization to pull secret scanning resultsARCHODEX_SECRETS_GITHUB_TOKEN: Your GitHub Personal Access Token